课程 网络安全 期末复习
本来不太想写,但是还是有始有终吧…
Lec 17 Smart Transportation Security & ML security
课外拓展的部分,是老师的科研方向内容。关于交通这一方向现在很火,无论是搞sensor还是搞计算方向,未来的愿景就是自动驾驶和车辆互联。
老师讲了两个他们正在研究的场景,一个关于通过互联车辆发送的信息做交通灯的决策,一个是关于自动驾驶激光雷达识别障碍做行驶方向和速度的决策。内容挺简单,我很好奇老师是啥时候开始搞这方面的研究的,竟然是第一个hack自动驾驶?第一个🚥的决策会面临两种安全威胁:1.我就是要报复社会我不管,把所有的交通搞瘫痪。2.我就是图自个儿省事省时间,别人靠边站。他们研究的是第一种。主要的攻击就是spoofing,篡改车辆的位置和速度信息,或者拦截了信息拖着不发给控制中心,导致交通灯决策的延时很大。一般交通指示灯的决策会要求当前互联的车辆大于某个阈值,所以攻击者也可以伪造数据,产生很多的 ghost vehicles。
第二个场景关于激光雷达的攻击,跟前面差不多,篡改雷达传递的数据。不过怎么篡改能做到以假乱真呢?这就是值得研究的东西了。除了spoofing外,对sensor的攻击还有DoS攻击,可以针对雷达、激光雷达、摄像头、GPS等设备。
安全这方面的工作还挺有趣,找出别人的漏洞这件事本身就很吸引人,要是成功了成就感满满的。
还有一次 guest talk 讲对抗机器学习,没怎么听,当时看PPT还挺基础的加上口音听不太懂,好像是个日本人。只能自学稍稍了解一下咯。
对抗机器学习是一个机器学习与计算机安全的交叉领域。对抗机器学习旨在给恶意环境下的机器学习技术提供安全保障。由于机器学习技术一般研究的是同一个或较为稳定的数据分布,当部署到现实中的时候,由于恶意用户的存在,这种假设并不一定成立。比如研究人员发现,一些精心设计的对抗样本(adversarial example)可以使机器学习模型失败输出正确的结果。
Szegedy等人在2013年首次提出对抗样本的存在以及生成方式之后,攻击与防御的方式已经经过几轮的迭代,从白盒到黑盒的攻击与防御。随着MLaaS的流行,另一种攻击方式:训练集毒化攻击——通过污染训练集来改变训练模型,也紧接被提出。
常见的防御方法有:对抗训练、梯度掩码、随机化、去噪等。
如果只了解个粗浅的表面还挺简单的,可以参考这篇文章 和 这篇文章。此外,这门课提供了一个研究入门指南,列出了一些该方向的论文。
考试指引:You need to know AV technology, its current background, possible attack surface, and possible consequences
Lec 16: Network Security/Threats
background
Internet Structure

Data Formats

TCP -> 全称 Transmission Control Protocol(我记得以前有人考过我,我没答出来…)Sequence number / ACK
IP -> 全称 Internet Protocol Unreliable / “best-effort” / Longest-prefix match

ICMP -> 全称 Control Message Protocol
- Provides feedback about network operation
- Out-of-band (control) messages carried in IP packets
- Error reporting, congestion control, reachability, etc.
Security Issues in TCP/IP
- packets pass untrusted hosts
- Eavesdropping (packet sniffing)
- IP addresses are public
- E.g., Ping-of-Death, Smurf attacks
- TCP connection requires state
- SYN flooding
- TCP state easy to guess
- TCP spoofing and connection hijacking
Packet Sniffing
早期应用程序:unencrypted data
Network Interface Card (NIC), e.g., Ethernet device, in “promiscuous mode” (混杂模式) can read all data on its broadcast segment
Solution: encryption (e.g., IPsec), improved routing
“Smurf” Attack

Solution: reject external packets to broadcast addresses
“Ping of Death”
When an old Windows machine receives an ICMP packet with payload over 64K, it crashes and/or reboots
Solution: patch OS, filter out ICMP packets
SYN Flooding
TCP Handshake:

Attack:

Attacker sends many connection requests (SYNs) with spoofed source (IP) addresses.
Victim allocates resources for each request. New thread, connection state maintained until timeout. Fixed bound on half-open connections.
Once server resources are exhausted, requests from legitimate clients are denied.
这里不是很懂????Other examples
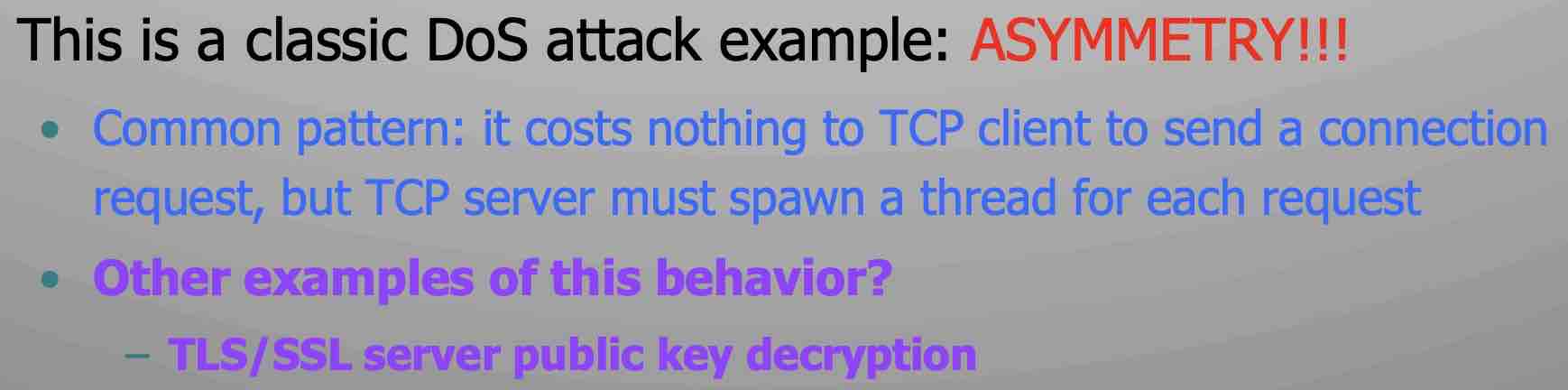
DoS is caused by asymmetric state allocation.
Solution1: Cookies allow server to remain stateless until client produces: Server state (IP addresses and ports) stored in a cookie and originally sent to client. When client responds, cookie is verified.

If source IP address is bogus, attacker can’t confirm 这个地方很不理解??前面都伪造了SYN,凭啥ACK无法伪造???
Solution2: Passive Defense - Random Deletion. Legitimate connections have a chance to complete Fake addresses will be eventually deleted.

TCP Connection Spoofing
TCP state is easy to guess (Port numbers are standard, seq numbers are predictable)
Can inject packets into existing connections: Guessing a 32-bit seq number is not practical, BUT most systems accept a large window of sequence numbers. SO send a flood of packets with likely sequence numbers
DoS by Connection Reset
If attacker can guess the current sequence number for an existing connection, can send a reset packet to close it (RST flag=1 in TCP header). Especially effective against long-lived connections.
Solution:
- Above transport layer: Kerberos
- Provides authentication, protects against application layer spoofing
- Does not protect against connection hijacking
- Above network layer: SSL/TLS and SSH
- Protects against connection hijacking and injected data
- Does not protect against DoS by spoo fed packets
- Network (IP) layer: IPsec
- Protects against hijacking, injection, DoS using connection resets, IP address spoofing
- But muddled/poor key management…
DNS: Domain Name Service
DNS responses are cached. Cached data periodically times out
DNS “Authentication”

DNS Spoofing / DNS Cache Poisoning


If attacker loses, has to wait until TTL expires. If attacker wins, future DNS requests for www.foo.com will go to 6.6.6.6.
Solution: DNSSEC
Goals: authentication and integrity of DNS requests and responses
PK-DNSSEC (public key)
- DNS server signs its data (can be done in advance)
- How do other servers learn the public key?
考试指引:You need to know and understand how different types of TCP/IP attacks and their corresponding defenses work
Lec 15: Transport Layer Security/Secure Socket Layer (TLS/SSL)
熟悉的配方,经典的计网PPT模版又出现了。
SSL: Secure Sockets Layer
TLS: Transport Layer Security
- Most widely deployed security protocol
- supported by almost all browsers, web servers
- the “s” in https
- billions $/year over SSL
- Current version:
- TLS = Transport Layer Security
- TLS 1.3: https://tools.ietf.org/html/rfc8446
provides
- confidentiality
- integrity
- authentication
original goals:
- Web e-commerce transactions encryption (especially credit-card numbers)
- Web-server authentication
- optional client authentication
- minimum hassle(麻烦) in doing business with new merchant
available to all TCP applications
- secure socket interface
- SSL/TLS provides application programmin interface (API) to applications
- C and Java SSL/TLS libraries/classes readily available

Toy SSL/TLS
handshake: Alice and Bob use their certificates, private keys to authenticate each other and exchange a shared secret

key derivation: Alice and Bob use shared secret to derive set of keys

data transfer: data to be transferred is broken up into series of records

connection closure: special messages to securely close connection

Summary

除此之外,Toy SSL/TLS 还包含了 fields长度、encryption algorithms、parameter negotiatio 等等
SSL/TLS Cipher Suite

Real SSL/TLS

why two random nonces?

SSL/TLS Record Protocol

SSL/TLS Record Format

Real SSL/TLS Connection

考试指引:
- You need to know how TLS/SSL works (how they can establish secure communication) and potential attacks on it
- You don’t need to memorize specific algorithms (e.g. symmetric key encryption, MAC) for SSL/TLS Cipher Suite.